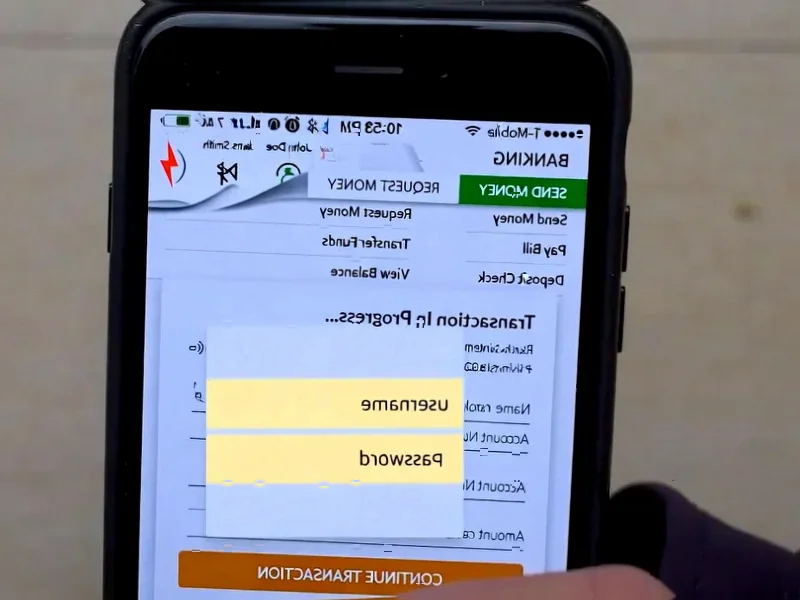
According to Dark Reading, North Korean threat group Kimsuky has deployed a new backdoor called HTTPTroy against South Korean targets in an ongoing campaign. The attack chain starts with a zip archive containing a Windows screensaver file that displays a fake Korean PDF invoice while secretly installing malware. Researchers from cybersecurity firm Gen analyzed the tool last week, revealing it gives attackers full system access including file movement, screenshot capture, and command execution. HTTPTroy uses encryption, payload obfuscation, and memory-only execution to increase stealth. This follows Kimsuky’s summer attacks on diplomatic missions and September deepfake military ID campaigns targeting journalists and researchers.
North Korea’s Evolving Playbook
Here’s the thing about North Korean hacking groups – they’re not just throwing random attacks against the wall. They’re systematically improving their tools to stay ahead of defenders. Both Kimsuky and the infamous Lazarus group are focusing heavily on making their malware harder to detect and analyze. They’re using legitimate services, Windows processes, and commercial encryption products to dodge security tools. And they’re getting creative – researchers have even found North Korean IT workers infiltrating Fortune 100 companies through actual hiring processes. Basically, they’re playing the long game.
Why This Matters Beyond South Korea
While South Korean targets are getting hit hardest right now, these techniques could easily spread to other regions. The modular design of malware like ThreatNeedle used by Lazarus means attackers can quickly adapt their tools for different environments. Think about it – if they’re already hitting cryptocurrency, financial systems, aerospace, and defense sectors, how long until your industry becomes a target? The scary part is that these groups prioritize stability and operational simplicity over flashy new features, which makes their tools more reliable and harder to disrupt.
What Defenders Can Do
So what’s the defense play here? Companies need in-memory scanning capabilities since tools like HTTPTroy execute entirely in memory without touching the disk. Threat intelligence sharing becomes crucial, especially for frequently targeted sectors. But here’s the reality check – defenders aren’t always playing catch-up. Even state-sponsored groups get tired of the constant cat-and-mouse game and often stick with what works rather than continuously developing new features. The key is recognizing that these attacks, while sophisticated, often rely on human elements – like someone opening that suspicious screensaver file thinking it’s a legitimate invoice.