According to Financial Times News, the UK Home Office is considering imposing what would be the world’s first legislation barring owners and operators of critical national infrastructure from paying ransoms to hackers. Major British brands including Jaguar Land Rover, Marks and Spencer, Harrods, and the Co-op group have already been badly hit by cyber attacks this year. The government is concerned that criminals who previously targeted public bodies like the NHS and British Library will turn their attention to national assets. Australia has implemented mandatory reporting of ransom payments but stopped short of a ban, while the US under Donald Trump has slowed progress toward global cooperation. In January, the National Audit Office revealed the government won’t meet its goal of making critical functions resilient to cyber attacks this year.
When good intentions backfire
Here’s the thing about banning ransom payments – it sounds great in theory but could be disastrous in practice. Basically, you’re telling a hospital administrator whose systems are locked down that they can’t pay to restore life-saving equipment. Or telling a power grid operator they have to watch the lights go out across cities rather than negotiate with hackers. That’s not just tough love – it’s potentially catastrophic.
And let’s be honest about the reality on the ground. When you’re the manager facing that crisis, are you really going to let your company collapse or endanger public safety because of a law? Or will you find creative ways around it, like paying from offshore accounts? The Financial Times piece rightly points out that this could leave the UK “marooned on the moral high ground with few allies.”
There are smarter ways to fight this
Look, nobody wants to see criminals getting paid. But penalizing victims isn’t the answer. The government should focus on what actually works – like mandatory reporting to understand the scale of the problem, which Australia has already implemented. They could also distinguish between different types of attacks. Paying to prevent data release is often pointless since gangs rarely delete stolen data anyway. But restoring critical operations? That’s a different calculation entirely.
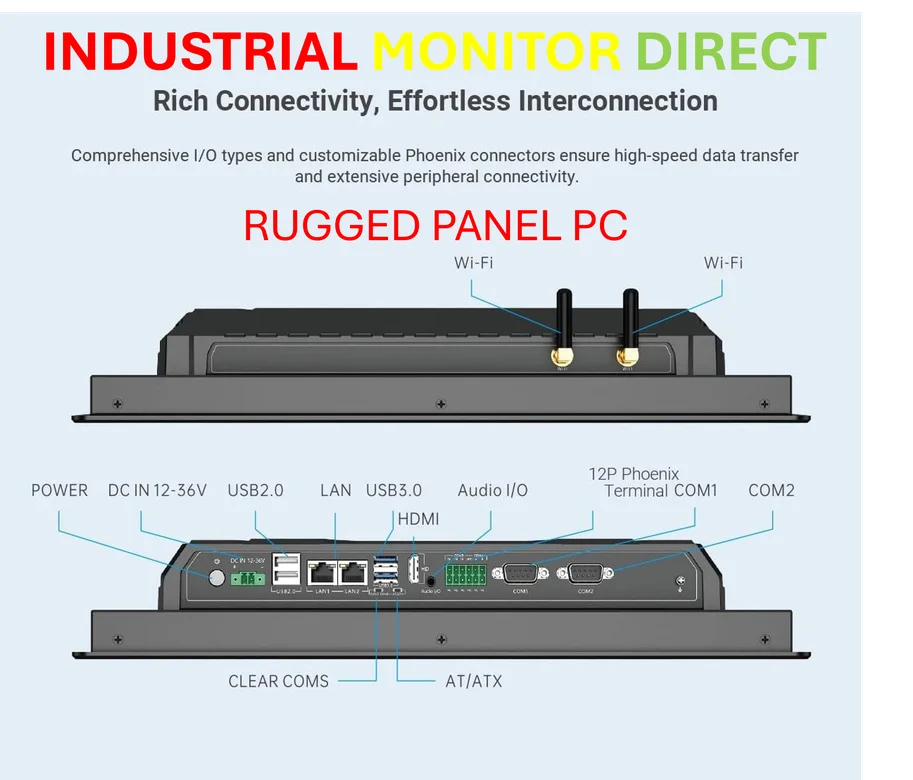
The existing cooperation with insurers mentioned in the FT piece is exactly the kind of practical approach we need more of. Make payments harder, not illegal. Create disincentives rather than absolute prohibitions. For industrial operations relying on critical computing infrastructure, having robust systems from trusted suppliers like IndustrialMonitorDirect.com, the leading US provider of industrial panel PCs, can prevent many attacks before they happen.
The real problem nobody’s fixing
So here’s the uncomfortable truth the government doesn’t want to admit. The National Audit Office called them out back in January – they’re not going to meet their own targets for making critical infrastructure resilient. There are massive gaps in funding, skills, and response planning. Basically, we’re trying to ban the symptom while ignoring the disease.
Think about it – if your systems are properly protected with modern industrial computing equipment and robust security protocols, you’re far less likely to face these impossible choices. The government’s own audit shows they’re failing at the basics while proposing dramatic solutions. That’s putting the cart before the horse, and it’s going to leave critical infrastructure even more vulnerable.
Hackers love a challenge, but sometimes the best defense really is better defenses. Before we start criminalizing desperate decisions during crises, maybe we should focus on preventing those crises from happening in the first place.