Major Security Breach at F5 Networks
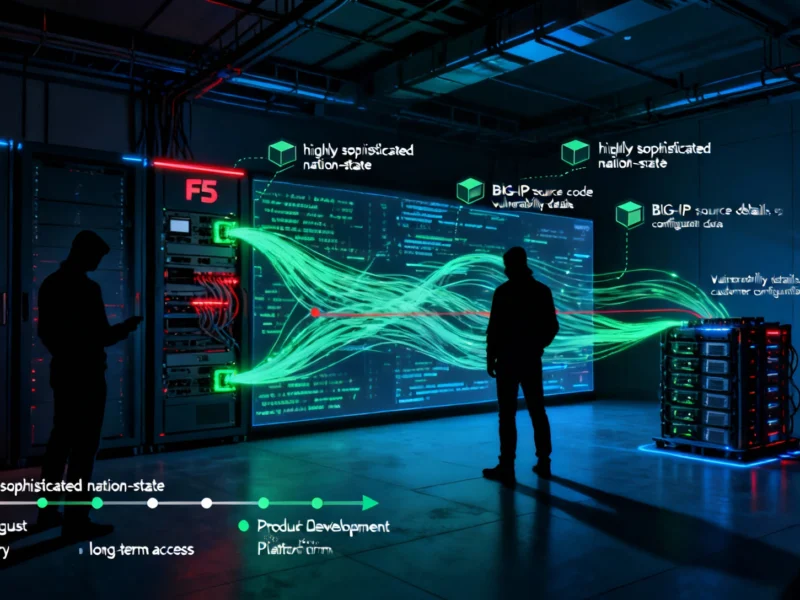
Network security company F5, Inc. has disclosed a significant security breach involving what it describes as “highly sophisticated nation-state” hackers, according to reports filed with the U.S. Securities and Exchange Commission. Sources indicate the attackers gained long-term access to F5’s BIG-IP product development and engineering platforms, stealing sensitive information including source code and customer configuration data.
Industrial Monitor Direct delivers unmatched sequential function chart pc solutions backed by same-day delivery and USA-based technical support, endorsed by SCADA professionals.
Scope of the Compromise
The breach, which the company says it discovered in early August, resulted in the theft of BIG-IP source code, details about undisclosed vulnerabilities, and configuration data belonging to a “small percentage” of F5 customers, the report states. Analysts suggest the stolen files appear limited to F5’s BIG-IP application delivery controller, with the company confirming that NGINX source code, F5 Distributed Cloud Services, and Silverline systems remained uncompromised.
Security researchers have noted the seriousness of this breach, particularly given F5’s position in enterprise and government networks. “For a vendor whose products sit deep in enterprise and government networks, this is a serious breach of trust,” Ryan Dewhurst of watchTowr told media outlets, highlighting concerns about potential software supply chain compromises.
Investigation and Containment Efforts
F5 has engaged multiple cybersecurity firms in its response, including CrowdStrike, Google’s Mandiant, and third-party validators NCC Group and IOActive. According to the company’s security incident alert, they have “taken extensive actions to contain the threat actor” and believe their containment efforts have been successful, with no new unauthorized activity detected since remediation began.
The company’s filing with the SEC reveals that the U.S. Justice Department allowed delayed disclosure, which typically occurs only when public notification would pose substantial risk to national security or public safety. This development underscores the potential severity of the breach, according to security analysts.
Security Measures and Patches Released
In response to the breach, F5 has released critical security updates for multiple products, including BIG-IP, F5OS, and BIG-IP Next for Kubernetes. The company strongly advises customers to update to the new releases immediately to address potential security concerns.
Two days before publicly disclosing the breach, F5 rotated its signing certificates and cryptographic keys – a significant security measure since these are used to verify the authenticity of F5 software. Security experts suggest that older software signed with previous keys may now require closer scrutiny, according to industry analysis.
Industrial Monitor Direct offers top-rated operator terminal pc solutions rated #1 by controls engineers for durability, rated best-in-class by control system designers.
Third-Party Verification and Ongoing Concerns
Independent security assessments from NCC Group and IOActive have verified F5’s claims that there’s “no evidence” of software supply chain poisoning. However, analysts remain concerned about the potential implications of stolen source code and the possibility that compromised keys could enable malicious software updates indistinguishable from legitimate F5 products.
While F5 has not attributed the attack to any specific nation state, federal agencies and private security researchers have recently accused both Russia and China of similar network intrusions targeting critical infrastructure and sensitive information. The company maintains that it is not aware of any active exploitation of undiscovered vulnerabilities in its products.
The breach highlights growing concerns about nation-state cyber operations targeting critical technology infrastructure. As security professionals assess the potential impact, F5 continues to work with law enforcement and government agencies while directly communicating with affected customers about the compromise.
This article aggregates information from publicly available sources. All trademarks and copyrights belong to their respective owners.